(istvan@louisiana.edu)
0. Introduction
Since election day, there has been a plethora of concerns, conspiracy theories, criticisms and commentaries on the events of that evening and night. Many of these issues have been raised on Internet sites, such as http://www.blackboxvoting.org, http://www.blackboxvoting.com, http://www.votersunite.org and http://www.truthout.org. The site http://www.moveon.org has even started an Internet based petition that the election should be subject to detailed scrutiny.
Many of the concerns expressed have been nebulous in the extreme, focusing on all sorts of issues. For instance, the electronic polling machines have come in for particular criticism. The purpose of this is to address in specific detail a potential electoral problem that has not received too much attention, this concerns the tabulating machines. It will be shown that there are specific potential problems with these devices. A detailed technical description of these problems will be provided, along with an illustrated example. It will then be argued that there is evidence that this is not just a theoretical issue.
1. Voting and Reporting
It is important that the mechanisms actually used in U.S. elections are understood. Although there are many variations, due to different States having different legislation, there are certain commonalities to the structure, especially with respect to the chain of reporting of ballots cast. Each State is divided into administrative regions. These can be Counties, Parishes, Wards, or Districts. The important point is that the ballot totals from each polling place is reported to these administrative regional headquarters. These headquarters then report tabulated tallies to a central Statewide location. This reporting structure is pretty much universal and is entirely independent of the actual technology used to record the individual voters' choices, be it punch card, optically scanned ballot, or entirely electronic voting technologies.
The reason why it is important that this structure is understood is that a problem within this structure can effect the outcome of almost any election. In the current context, the focus will be upon the so-called 'tabulating machines' that collect the reports from the individual polling places at the regional headquarters, add them up and then report to further tabulators at the State level. It turns out that this tabulating and reporting process is a particular cause of concern.
2. Tabulating and Reporting Systems
A variety of technologies are used in the process of adding up the votes. In order to make this account as concrete as possible, attention will be focused on a particular system, GEMS (Global Election Management System), sold by the Diebold Corporation. GEMS is a suite of software that runs on an ordinary Windows computer. Votes can be reported to the system in a variety of ways, ranging from polling places making dial-up connections to the computer by modem, or by the system scanning memory cards.
A version of the GEMS software is available on the Internet at http://www.blackboxvoting.org. The discussion here is based upon this version of the software, version 1.18.15.0 (2002), a prerelease version. At the same web site, a real set of election results is available. These are the results from The City of Colorado Springs Election, that took place on April 3rd, 2001. These are the results that will be used for the illustration below.
3. GEMS: Operating System and Physical Security
The Windows operating system is an immediate cause for concern. Although many of us run it on our home and office computers, regular concerns about the security of this operating system appear on technological web sites, such as http://slashdot.org on a regular basis. Although Microsoft addresses security issues on a regular basis, a machine is only truly secure if it has been thoroughly patched and subject to a very detailed security audit. So, the security of the machine upon which GEMS runs is a function of the zealousness of the information technology staff of each location where GEMS is deployed.
There is a further concern that arises with respect to the physical security of the GEMS system. Even if the operating system is completely up to date and maintained to the highest standards, any individual who has physical access to the machine may potentially access the files on the machine, including the files used by the GEMS system. This is due to the many well know ways of defeating Windows password security. For instance, if the system is booted from certain types of software media, administrator access to the machine can be gained with ease. Should this happen, all the flies and software on the machine can be accessed and potentially tampered with, by a person with malicious intent. It is perhaps significant that Microsoft do not recommend Windows for 'mission critical' situations. Whilst security issues are obviously crucial when it comes to crucial infrastructure, such as nuclear power stations, it is perhaps grounds for concern that it is considered acceptable for the tabulation of an election.
4. GEMS: Running the System
GEMS launches just like any other Windows program. However, it does have certain security features built in. Most notably when GEMS launches, it invites the user to select a particular election database file. Before the database will open in GEMS though, a password is required. This screen is illustrated below [sorry about the quality of the images -- these were the best that could be generated with the available equipment].
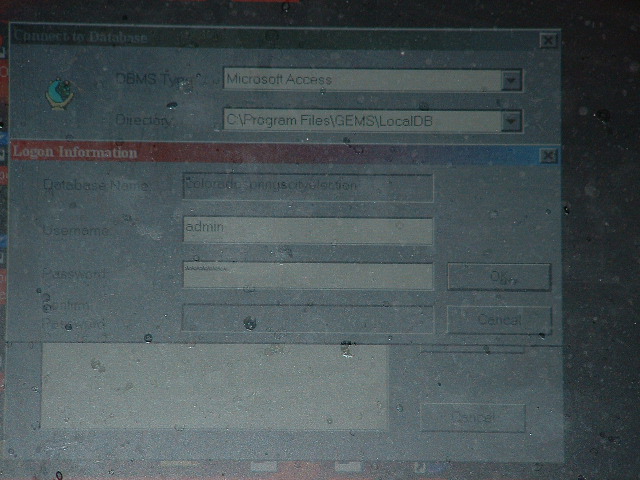
Of course, the security of GEMS is contingent upon the care with which the password was chosen. In this case, the password was just 'password'. Clearly this is not satisfactory.
Once the password has been successfully entered, it becomes possible to use GEMS. The user is presented with a range of menus and options, as can (almost) be seen in the following screen shot.

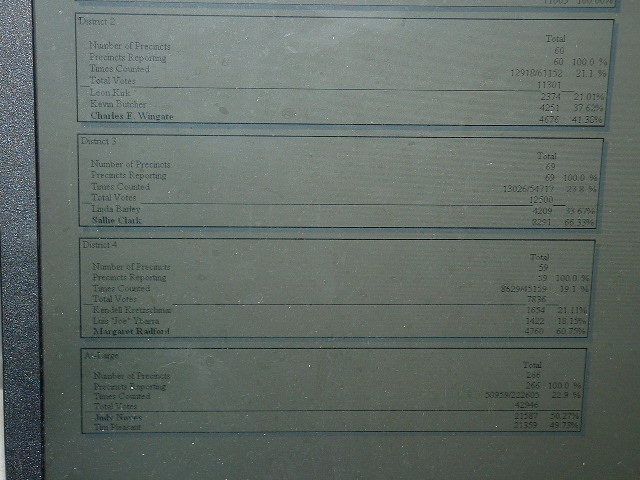
Along the top is a series of menu options. One of these can be used to generate reports from the loaded election database. The picture below illustrates part of an 'Election Summary Report' based upon the Colorado Springs election results.
Since election day, there has been a plethora of concerns, conspiracy theories, criticisms and commentaries on the events of that evening and night. Many of these issues have been raised on Internet sites, such as http://www.blackboxvoting.org, http://www.blackboxvoting.com, http://www.votersunite.org and http://www.truthout.org. The site http://www.moveon.org has even started an Internet based petition that the election should be subject to detailed scrutiny.
Many of the concerns expressed have been nebulous in the extreme, focusing on all sorts of issues. For instance, the electronic polling machines have come in for particular criticism. The purpose of this is to address in specific detail a potential electoral problem that has not received too much attention, this concerns the tabulating machines. It will be shown that there are specific potential problems with these devices. A detailed technical description of these problems will be provided, along with an illustrated example. It will then be argued that there is evidence that this is not just a theoretical issue.
1. Voting and Reporting
It is important that the mechanisms actually used in U.S. elections are understood. Although there are many variations, due to different States having different legislation, there are certain commonalities to the structure, especially with respect to the chain of reporting of ballots cast. Each State is divided into administrative regions. These can be Counties, Parishes, Wards, or Districts. The important point is that the ballot totals from each polling place is reported to these administrative regional headquarters. These headquarters then report tabulated tallies to a central Statewide location. This reporting structure is pretty much universal and is entirely independent of the actual technology used to record the individual voters' choices, be it punch card, optically scanned ballot, or entirely electronic voting technologies.
The reason why it is important that this structure is understood is that a problem within this structure can effect the outcome of almost any election. In the current context, the focus will be upon the so-called 'tabulating machines' that collect the reports from the individual polling places at the regional headquarters, add them up and then report to further tabulators at the State level. It turns out that this tabulating and reporting process is a particular cause of concern.
2. Tabulating and Reporting Systems
A variety of technologies are used in the process of adding up the votes. In order to make this account as concrete as possible, attention will be focused on a particular system, GEMS (Global Election Management System), sold by the Diebold Corporation. GEMS is a suite of software that runs on an ordinary Windows computer. Votes can be reported to the system in a variety of ways, ranging from polling places making dial-up connections to the computer by modem, or by the system scanning memory cards.
A version of the GEMS software is available on the Internet at http://www.blackboxvoting.org. The discussion here is based upon this version of the software, version 1.18.15.0 (2002), a prerelease version. At the same web site, a real set of election results is available. These are the results from The City of Colorado Springs Election, that took place on April 3rd, 2001. These are the results that will be used for the illustration below.
3. GEMS: Operating System and Physical Security
The Windows operating system is an immediate cause for concern. Although many of us run it on our home and office computers, regular concerns about the security of this operating system appear on technological web sites, such as http://slashdot.org on a regular basis. Although Microsoft addresses security issues on a regular basis, a machine is only truly secure if it has been thoroughly patched and subject to a very detailed security audit. So, the security of the machine upon which GEMS runs is a function of the zealousness of the information technology staff of each location where GEMS is deployed.
There is a further concern that arises with respect to the physical security of the GEMS system. Even if the operating system is completely up to date and maintained to the highest standards, any individual who has physical access to the machine may potentially access the files on the machine, including the files used by the GEMS system. This is due to the many well know ways of defeating Windows password security. For instance, if the system is booted from certain types of software media, administrator access to the machine can be gained with ease. Should this happen, all the flies and software on the machine can be accessed and potentially tampered with, by a person with malicious intent. It is perhaps significant that Microsoft do not recommend Windows for 'mission critical' situations. Whilst security issues are obviously crucial when it comes to crucial infrastructure, such as nuclear power stations, it is perhaps grounds for concern that it is considered acceptable for the tabulation of an election.
4. GEMS: Running the System
GEMS launches just like any other Windows program. However, it does have certain security features built in. Most notably when GEMS launches, it invites the user to select a particular election database file. Before the database will open in GEMS though, a password is required. This screen is illustrated below [sorry about the quality of the images -- these were the best that could be generated with the available equipment].
Of course, the security of GEMS is contingent upon the care with which the password was chosen. In this case, the password was just 'password'. Clearly this is not satisfactory.
Once the password has been successfully entered, it becomes possible to use GEMS. The user is presented with a range of menus and options, as can (almost) be seen in the following screen shot.
Along the top is a series of menu options. One of these can be used to generate reports from the loaded election database. The picture below illustrates part of an 'Election Summary Report' based upon the Colorado Springs election results.
Attention should be directed to the bottom of the
picture, where the results for an 'At-Large' race are reported.
According to GEMS, Judy Noyes won this race with 21,587 votes (50.27%).
Her opponent was Tim Pleasant who received 21,359 votes (49.73%). So
far, so good. However, this is also where it is possible to begin to
demonstrate some of the shortcoming of the system.
5. GEMS: Making Changes
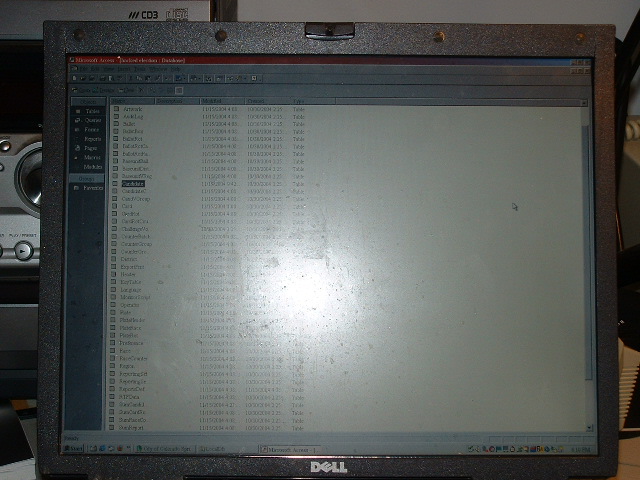
With the GEMS software still running, it is also possible to access the election results by other means. In particular, the database software upon which GEMS is based, is the common Access database software that ships with many versions of Microsoft's popular Office suite of programs. The following picture illustrates the database for the Colorado Springs election open in Access, whilst it is also open in GEMS!
5. GEMS: Making Changes
With the GEMS software still running, it is also possible to access the election results by other means. In particular, the database software upon which GEMS is based, is the common Access database software that ships with many versions of Microsoft's popular Office suite of programs. The following picture illustrates the database for the Colorado Springs election open in Access, whilst it is also open in GEMS!
Perhaps the most worrying aspect of this ability
to simultaneously open the database in GEMS and Access is that Access
does not require the user to supply any password at all, to get at the
data contained in the database.
Once Access has opened the GEMS database, simply double clicking on a database component causes it to be opened. In addition, the file can be edited. The picture below illustrates the Candidates component of the Colorado Springs city election. This contains the candidates names and various other bits of information, including the internal indexing variable, used by GEMS.
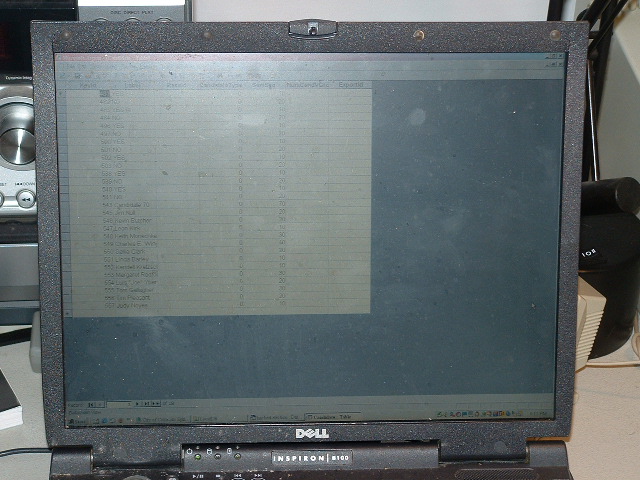
The close up detail of the Candidates component of the Colorado Springs city election is illustrated below. The indexing variable and the candidate names are visible.

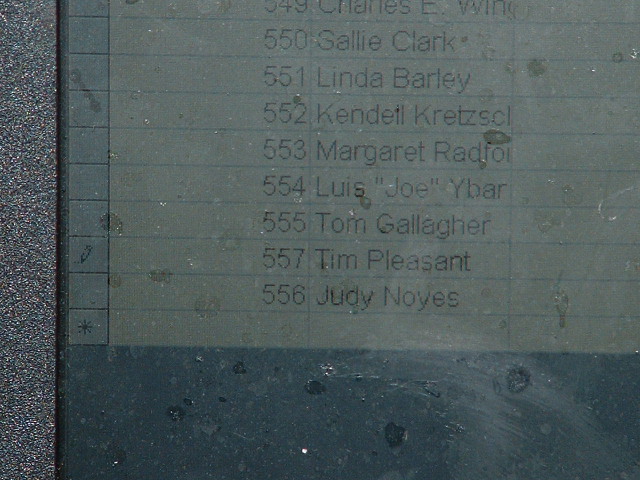
Once Access has opened the GEMS database, simply double clicking on a database component causes it to be opened. In addition, the file can be edited. The picture below illustrates the Candidates component of the Colorado Springs city election. This contains the candidates names and various other bits of information, including the internal indexing variable, used by GEMS.
The close up detail of the Candidates component of the Colorado Springs city election is illustrated below. The indexing variable and the candidate names are visible.
The important point in the current context is to
note that candidate Tim Pleasant has index number '556' and his
opponent in the At Large race, Judy Noyes has the index number 557.
Here is where is gets scary. It is a trivial matter to just reverse the
index numbers. This is illustrated in the next picture.
It turns out that this simple change has a
dramatic effect upon the apparent outcome of the election. This is
despite the fact that the change could be made without needing a
password in under thirty seconds. Of course, after the change has been
made, it is also necessary to save the new version of the file. Once
the change had been made, GEMS was reexamined, so as to view the effect
that it had (remember GEMS has been running throughout this exercise).
Pulling up the Election Summary report equivalent to the one that was
illustrated at the end of the last section, produces the following
result.
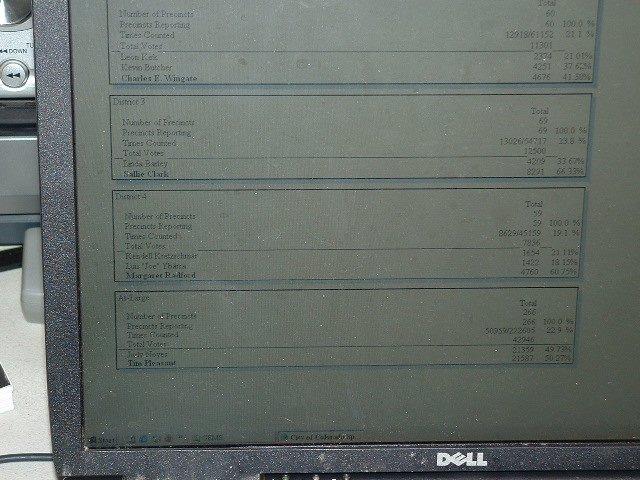
Although the picture isn't as clear as it might
be, it is clear that in this case Tim Pleasant's name is bolded as the
winner of the race. He now appears to have 21,587 votes (50.27%) in
contrast to the 21,359 (49.73%) assigned to Judy Noyes by the altered
GEMS database. What the simple change in the index number has effected is a trading of one candidates votes with the other!
6. GEMS: Audit Logs
Although this result is somewhat shocking, all hope should not be lost. GEMS maintains an elaborate and detailed audit logs that keep a record of every activity of the system. This is a sensible and prudent provision on the behalf of the system's manufacturer. So, it is to be hoped that such an obviously fraudulent change (at least fraudulent in the context of a real election) should be recorded in the Audit logs of the system. The picture below provides an illustration of the kind of information that appears in the GEMS audit log.
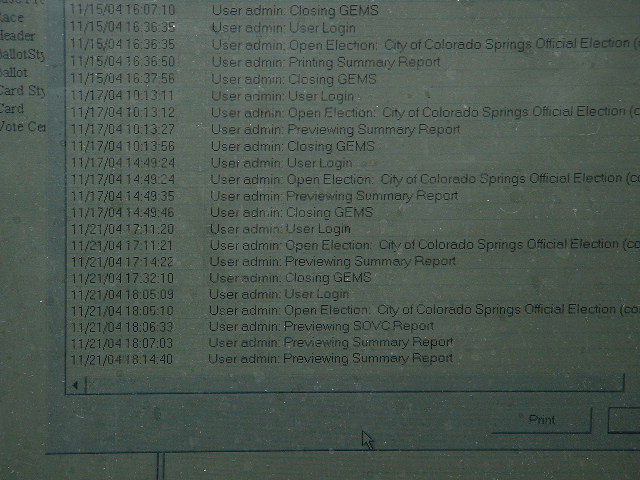
6. GEMS: Audit Logs
Although this result is somewhat shocking, all hope should not be lost. GEMS maintains an elaborate and detailed audit logs that keep a record of every activity of the system. This is a sensible and prudent provision on the behalf of the system's manufacturer. So, it is to be hoped that such an obviously fraudulent change (at least fraudulent in the context of a real election) should be recorded in the Audit logs of the system. The picture below provides an illustration of the kind of information that appears in the GEMS audit log.
The system, clearly identifies activity in the
system, records which user was responsible and the precise date and
time the activity occurred. In the current context, the last four
entries are of crucial interest. The entry at 18.05 corresponding to
the opening of GEMS for the session illustrated in the pictures above.
The 18.07 entry corresponds to the original displaying of the Election
Summary Report included in section 4, above, prior to changes having
been made to the database. The final entry at 18.14 is the second
version of the same report displayed after the changes had been made.
However, GEMS contains no record that the election database has been tampered with!
This is because the changes were made outside the system and, as such,
could not be logged by the system. (N.B. although it took under 30
seconds to make the changes in Access, taking pictures of the process
is the reason for the apparently longer time indicated here).
This particular result is especially troubling. It shows that even though the system has a number of safeguards within it to prevent tampering, these safeguards can easily be circumvented. This problem is especially troublesome for jurisdictions that use voting technologies that produce no paper ballot. This is because if such a change was made, there would be no way to know that it had happened and no method of verifying the results of the election.
7. Caveats and Discussion
The example illustrated above should certainly provide election officials who use GEMS with cause for concern. Of course, it is important to stress that the version of the software is a prerelease version. It is quite possible that the shortcomings illustrated here may have been fixed. However, it would at the very least be prudent to check that this is the case. Probably a better solution would be for all results that were tabulated using GEMS should be subject to a statistically meaningful partial hand count, where ever possible. It is also important to realize that GEMS is not the only tabulating system used in the election of November 2nd this year. It would also appear prudent that other systems be checked for similar problems. Until such after the fact checks have been undertaken, concerns about the validity of the results will remain.
Denial is a natural reaction to such demonstrations of problems, especially in the highly politically charged context of the recent Presidential campaign. One obvious line of defense would be for election officials to note that the Microsoft Access software was not installed on their machines that ran GEMS. Such a defense is without virtue however. This is because it is a simple matter to have Access installed on a portable storage media, like a so-called 'thumb drive'. It would be trivial to insert such a drive into a USB port for the short duration need to make the changes and then remove it, leaving no obvious trace that it had ever been there.
8. Could this really ever have happened?
Thus far a possibility of a problem has been demonstrated, but nothing more. Many things are possible, rather fewer are actual. So, in the current context, it is important to consider whether there is any evidence that the kind of situation illustrated above might hove occurred in a real election. Regrettably, the evidence suggests that something akin to the situation described above may have actually occurred on more than one occasion. So, yes this really could have happened.
The activist web site http://www.votersunite.org has a list of problems that have arisen with election technology, organized by vendor. The document covering Diebold machines at http://www.votersunite.org/info/Dieboldinthenews.pdf lists the following instances:
There are however further grounds for concern, especially with respect to the recent Presidential election of November 2004. These concerns focus upon the various discrepancies that have been reported between the results from exit polls and final vote tallies. Steven F. Freeman, Ph.D for the University of Pennsylvania has provided an analysis of these alleged discrepancies that is available at http://truthout.org/unexplainedexitpoll.pdf. According to Freeman, exit polls usually have a very low margin of error. He cites claims that discrepancies between exit polls and final election results are usually in the region of 0.2%. In the recent Presidential election, Freeman's analysis suggest that discrepancies were much larger than this. After offering the details of his methodology he concludes that there were significant and troubling discrepancies in the States of Ohio, Florida and Pennsylvania such that the odds against these discrepancies occurring in three States were on the order of 250 million to one, against. The case of Ohio is especially troubling in the context of the illustration offered above. Freeman's data indicates that exit polls suggested that Bush would receive 47.9% of the vote and Kerry would receive 52.1%. The final results though showed that, according to the official totals, Bush was actually assigned 51.0% of the vote, as compared to Kerry's 48.5%. Analogous reversals can also be seen in the case of Nevada and New Mexico, in addition. These reversals are especially troublesome, as they are the kind of thing that one might expect to see if techniques similar to the one above were employed at some of the locations where GEMS was used.
Various responses to this exit poll data have been offered. Freeman discusses with most of these and finds the explanations offered unsatisfactory. Perhaps the most salient issue in this context is that the exit polls were never intended to be used as a means of verifying the integrity of the election. However, intent is not always a useful way of assessing situations. After all, the drug Viagra was originally investigated as a heart medication! The evidence offered here makes it reasonable that these discrepancies should at the very least be examined much more carefully.
9. Conclusions
The information presented here obviously raises the question of whether it is possible that the recent Presidential election was rigged. Regrettably, the information does not provide a clear answer on this question. It is clear that using the techniques illustrated, the election could have been subject to tampering. For this reason then, it seems that there are compelling reasons that what evidence that remains should be subject to detailed scrutiny. More importantly though it also suggests that steps should be taken to ensure this situation never arises again.
This particular result is especially troubling. It shows that even though the system has a number of safeguards within it to prevent tampering, these safeguards can easily be circumvented. This problem is especially troublesome for jurisdictions that use voting technologies that produce no paper ballot. This is because if such a change was made, there would be no way to know that it had happened and no method of verifying the results of the election.
7. Caveats and Discussion
The example illustrated above should certainly provide election officials who use GEMS with cause for concern. Of course, it is important to stress that the version of the software is a prerelease version. It is quite possible that the shortcomings illustrated here may have been fixed. However, it would at the very least be prudent to check that this is the case. Probably a better solution would be for all results that were tabulated using GEMS should be subject to a statistically meaningful partial hand count, where ever possible. It is also important to realize that GEMS is not the only tabulating system used in the election of November 2nd this year. It would also appear prudent that other systems be checked for similar problems. Until such after the fact checks have been undertaken, concerns about the validity of the results will remain.
Denial is a natural reaction to such demonstrations of problems, especially in the highly politically charged context of the recent Presidential campaign. One obvious line of defense would be for election officials to note that the Microsoft Access software was not installed on their machines that ran GEMS. Such a defense is without virtue however. This is because it is a simple matter to have Access installed on a portable storage media, like a so-called 'thumb drive'. It would be trivial to insert such a drive into a USB port for the short duration need to make the changes and then remove it, leaving no obvious trace that it had ever been there.
8. Could this really ever have happened?
Thus far a possibility of a problem has been demonstrated, but nothing more. Many things are possible, rather fewer are actual. So, in the current context, it is important to consider whether there is any evidence that the kind of situation illustrated above might hove occurred in a real election. Regrettably, the evidence suggests that something akin to the situation described above may have actually occurred on more than one occasion. So, yes this really could have happened.
The activist web site http://www.votersunite.org has a list of problems that have arisen with election technology, organized by vendor. The document covering Diebold machines at http://www.votersunite.org/info/Dieboldinthenews.pdf lists the following instances:
The fact that these errors were discovered by election officials is good news and provides some assurances with respect to the electoral process. However, one is left wondering whether there were other incidents that were missed. These concerns are necessarily heightened in jurisdictions that no longer have a paper trail of paper ballots.
- In August 2002, an election in Clay County, Kansas had a problem. Initially it appeared that one candidate had won easily, however a recount reversed the result. Moreover in one ward, it was clear that the candidates totals had been reversed.
- In October 2003, during the California recall election, poll workers in Alamedia County noticed a sudden surge in votes from absentee ballots for the fringe candidate John Burton. An investigation revealed that votes cast for Lt. Gov. Cruz Bustamante were mysteriously being awarded to Burton.
- In the same election, Tulare County reported apparent voting trends which favored surprising candidates, whilst the major candidates received a very small proportion of the votes cast. In several counties that used the Diebold machines, candidate Jerry Kunzman received surprisingly high vote totals. Researchers from New York University hypothesized that these surprising trends were best explained by the shifting of votes between candidates.
- In March 2004, in the presidential primary race in San Diego County, California 2,747 votes cast for U.S. Sen. John Kerry were switched to U.S. Rep. Dick Gephardt.
There are however further grounds for concern, especially with respect to the recent Presidential election of November 2004. These concerns focus upon the various discrepancies that have been reported between the results from exit polls and final vote tallies. Steven F. Freeman, Ph.D for the University of Pennsylvania has provided an analysis of these alleged discrepancies that is available at http://truthout.org/unexplainedexitpoll.pdf. According to Freeman, exit polls usually have a very low margin of error. He cites claims that discrepancies between exit polls and final election results are usually in the region of 0.2%. In the recent Presidential election, Freeman's analysis suggest that discrepancies were much larger than this. After offering the details of his methodology he concludes that there were significant and troubling discrepancies in the States of Ohio, Florida and Pennsylvania such that the odds against these discrepancies occurring in three States were on the order of 250 million to one, against. The case of Ohio is especially troubling in the context of the illustration offered above. Freeman's data indicates that exit polls suggested that Bush would receive 47.9% of the vote and Kerry would receive 52.1%. The final results though showed that, according to the official totals, Bush was actually assigned 51.0% of the vote, as compared to Kerry's 48.5%. Analogous reversals can also be seen in the case of Nevada and New Mexico, in addition. These reversals are especially troublesome, as they are the kind of thing that one might expect to see if techniques similar to the one above were employed at some of the locations where GEMS was used.
Various responses to this exit poll data have been offered. Freeman discusses with most of these and finds the explanations offered unsatisfactory. Perhaps the most salient issue in this context is that the exit polls were never intended to be used as a means of verifying the integrity of the election. However, intent is not always a useful way of assessing situations. After all, the drug Viagra was originally investigated as a heart medication! The evidence offered here makes it reasonable that these discrepancies should at the very least be examined much more carefully.
9. Conclusions
The information presented here obviously raises the question of whether it is possible that the recent Presidential election was rigged. Regrettably, the information does not provide a clear answer on this question. It is clear that using the techniques illustrated, the election could have been subject to tampering. For this reason then, it seems that there are compelling reasons that what evidence that remains should be subject to detailed scrutiny. More importantly though it also suggests that steps should be taken to ensure this situation never arises again.
This page and the associated images are
subject to all Copyright laws 2004. However, permission is granted for
the material in this page to be reproduced, subject to the provisions
that (1) it is reproduced in its entirety, (2) it is not reproduced as
part of a profit making activity, (3) an acknowledgment of the source
is provided and (4) the author is notified by e-mail at istvan@louisiana.edu.
Permissions for other uses may be granted, be inquiries on this matter
should be sent to the same e-mail address. Comments and corrections
about this page should also be sent to this address.